We design, build, and run infrastructure, platforms, applications, and processes that enable cyber training for the integrated multi-domain force. CESI enables comprehensive training for the Cyber Mission Force as one of the core contractors building and running the Persistent Cyber Training Environment (PCTE) in support of the US Army and US Cyber Command.

sophisticated defenses
cyber operations & training environments
thinking beyond traditional IT security
Risk Management Framework (RMF) compliance is just the baseline of a good cybersecurity posture. We tailor RMF solutions to the system’s unique requirements and across its entire life cycle. We dive deep to understand both your compliance requirements and the additional hardening, monitoring, and support needed to provide true in-depth cybersecurity.
We apply our expertise in development, security, and operations (DevSecOps) as well as continuous integration and continuous delivery (CI/CD) automation to integrate cybersecurity throughout the entire system life cycle. We make certain that the systems and tools supporting the training of the Cyber Mission Force meet emerging requirements to protect, detect, and defend against real-world attacks and threats.

Some of our specialties include:
- End-to-end security design
- Vulnerability management
- Solutions for legacy, container, and cloud architectures
- Integrated performance and security monitoring

cyber training for cyber warriors
We have deep expertise in building cyber ranges utilizing the latest in virtualization and containerization technologies. We design, implement and operate physical data centers and utilize a software stack that is both on prem and cloud capable. We ensure that Cyber Mission Forces (CMFs) have a training capability that is always secure and always available, on a tech stack that is designed for the present and the future. We have expertise in the integration of physical hardware into the cyber ranges via secure “Hardware in the Loop” integrations, that function both on prem and remote. We bring the capability you need to ensure the cyber force is prepared for any engagement.
cyber training for multi-domain operations forces
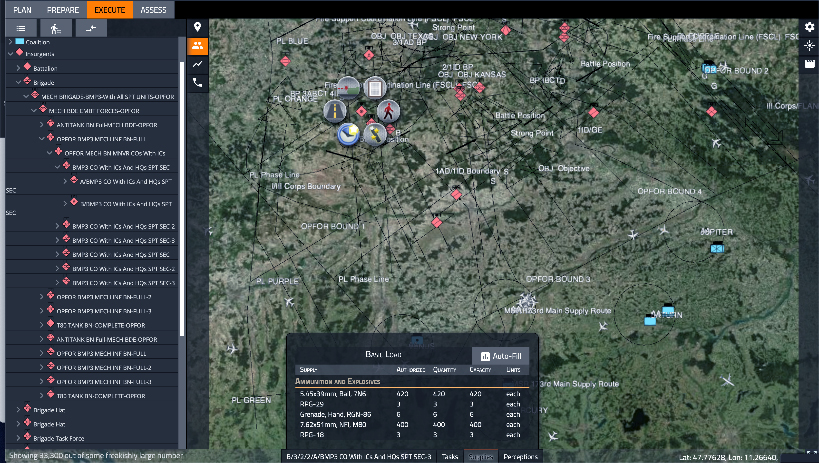
We apply our expertise in developing Modeling and Simulation (M&S) systems for the kinetic training, experimentation, and analysis communities to emerging cyber simulations and range platforms. We offer real-time cyber range integration with kinetic simulations through our MSSV next generation simulation framework. Additionally, our OpSim product enables modeling of integrated cyber and kinetic multi-domain operations in a modern, high-performance constructive simulation that includes these core features:
- Fully automated forces with human in-the-loop operation and interventions
- Intuitive, browser-based user interface supports visualization and control of forces
- Terrain reasoning for maneuver and sensing using objective terrain format databases
- Plans imported from SitaWare or from other military scenario definition language planning tools
- Utilizes pedigreed modeling with user editable spreadsheet performance and characteristics data
- Run simulation up to 1000x wall clock time

infrastructure as code (IaC)
IaC reduces the operational overhead and human error associated with deploying and updating complex hardware and software systems in data center and cloud environments. Systems can be stood up rapidly and consistently, with baked in security. Integrity monitoring solutions provide for continuous compliance validation and configuration drift avoidance against approved system configurations, designs and security compliance policies.
Our IaC automation solutions are used today to enable the operation, security and compliance of complex defense systems like the Persistent Cyber Training Environment (PCTE).
customized cyber solutions
We develop and operate enterprise-level cybersecurity functionality integrated with DevSecOps and agile software development lifecycle processes. We successfully implemented custom technical solutions using a combination of the latest commercial software tools, open source software tools, and system configurations to establish a strong security posture and provide transparency within environments. Our solutions deliver critical enterprise security functionality to our customers that includes:
- Identity and Access Management, supporting hundreds of user accounts
- Two-factor integration with DoD CAC
- Remote Patch Management
- Tiered architecture of local mirrored repositories to support multiple platforms
- Comprehensive vulnerability scanning
- Network Monitoring and Alerting
- Customized triggers and alerts